“You never change things by fighting the existing reality. To change something, build a new model that makes the existing model obsolete.”
Buckminster Fuller










The large circular stones pictured above known as Rai are an often cited example of how emergent monetary systems come into existence. These stone disks came to be recognized and utilized as the primary store of value and medium of exchange for an entire isolated civilization of peoples indigenous to the Micronesian island of Yap. As a compelling example of monetary policy in microcosm these stone disks came to be the primary monetary instruments utilized b the inhabitants of Yap due to their composition of limestone which is entirely absent on the isolated island.
“The curious task of economics is to demonstrate to men how little they really know about what they imagine they can design.” Friedrich August von Hayek


Tulip mania was a period during the Dutch Golden Age often cited by economists as the first example of an investment bubble and burst. Driven by an inflated market over the bulbs of the recently introduced and fashionable tulip combined with the speculation resulting from a then misunderstood genetic mutation which caused a striped coloration in a small percentage of flowers. These combined factors caused contract prices for some of these tulip bulbs to reach extraordinarily high levels, with the major acceleration starting in 1634 and then dramatically collapsing the entire Dutch economy in February 1637.







Stuart Haber in conjunction with W. Scott Stornetta pens the seminal, groundbreaking research paper "How to Time-Stamp a Digital Document” during their coincidental tenures at Bell Communications Research. Heralded as the document which first outlined blockchain technology the duo followed up on their research a year later with a complimentary paper that first suggested the use of Merkle trees as a means of compressing and bundling transactions together within a blockchain structure.
"A smart contract is a computerized transaction protocol that executes the terms of a contract. The general objectives of smart contract design are to satisfy common contractual conditions (such as payment terms, liens, confidentiality, and even enforcement), minimize exceptions both malicious and accidental, and minimize the need for trusted intermediaries. Related economic goals include lowering fraud loss, arbitration and enforcement costs, and other transaction costs."
"The success of the common law of contracts, combined with the high cost of replacing it, makes it worthwhile to both preserve and to make use of these principles where appropriate. Yet, the digital revolution is radically changing the kinds of relationships we can have. What parts of our hard-won legal tradition will still be valuable in the cyberspace era? What is the best way to apply these common law principles to the design of our on-line relationships?"
"New institutions, and new ways to formalize the relationships that make up these institutions, are now made possible by the digital revolution. I call these new contracts "smart", because they are far more functional than their inanimate paper-based ancestors. No use of artificial intelligence is implied. A smart contract is a set of promises, specified in digital form, including protocols within which the parties perform on these promises."

The science fiction novel Snow Crash authored by Neal Stephenson is published, from which the term Metaverse as well as numerous other tropes now common to the genre originate.

Abstract:
A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution. Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending. We propose a solution to the double-spending problem using a peer-to-peer network. The network timestamps transactions by hashing them into an ongoing chain of hash-based proof-of-work, forming a record that cannot be changed without redoing the proof-of-work. The longest chain not only serves as proof of the sequence of events witnessed, but proof that it came from the largest pool of CPU power. As long as a majority of CPU power is controlled by nodes that are not cooperating to attack the network, they'll generate the longest chain and outpace attackers. The network itself requires minimal structure. Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will, accepting the longest proof-of-work chain as proof of what happened while they were gone.
1. Introduction
Commerce on the Internet has come to rely almost exclusively on financial institutions serving as trusted third parties to process electronic payments. While the system works well enough for most transactions, it still suffers from the inherent weaknesses of the trust based model. Completely non-reversible transactions are not really possible, since financial institutions cannot avoid mediating disputes. The cost of mediation increases transaction costs, limiting the minimum practical transaction size and cutting off the possibility for small casual transactions, and there is a broader cost in the loss of ability to make non-reversible payments for non-reversible services. With the possibility of reversal, the need for trust spreads. Merchants must be wary of their customers, hassling them for more information than they would otherwise need. A certain percentage of fraud is accepted as unavoidable. These costs and payment uncertainties can be avoided in person by using physical currency, but no mechanism exists to make payments over a communications channel without a trusted party.What is needed is an electronic payment system based on cryptographic proof instead of trust, allowing any two willing parties to transact directly with each other without the need for a trusted third party. Transactions that are computationally impractical to reverse would protect sellers from fraud, and routine escrow mechanisms could easily be implemented to protect buyers. In this paper, we propose a solution to the double-spending problem using a peer-to-peer distributed timestamp server to generate computational proof of the chronological order of transactions. The system is secure as long as honest nodes collectively control more CPU power than any cooperating group of attacker nodes.
2. Transactions
We define an electronic coin as a chain of digital signatures. Each owner transfers the coin to the next by digitally signing a hash of the previous transaction and the public key of the next owner and adding these to the end of the coin. A payee can verify the signatures to verify the chain of ownership.



“If you don’t believe it or don’t get it, I don’t have the time to try to convince you, sorry.” Satoshi Nakamoto
"The root problem with conventional currency is all the trust that's required to make it work. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust." Satoshi Nakamoto
The first bitcoin exchange goes live. Initially proposed on the Bitcointalk forum by “dwdollar” on Jan. 15, 2010.


Although hard to pin down an exact date, by this time The Silk Road marketplace was fully operational and beginning to amass a sizable user base, facilitate a massive quantity of illicit transactions, and garner attention from authorities.


Vitalik Buterin publishes a whitepaper outlining a decentralized computation platform utilizing aspects of the bitcoin network such as proof of work while greatly expanding the utility offered over existing blockchains by implementing a Turing-complete scripting language..
As development began in earnest a team of core developers quickly formed around the initial proposal including Gavin Wood, Charles Hoskinson,Joseph Lubin and Jeffrey Wilcke. In July of 2014 a public crowd-sale provided the initial financing for the project, and later in that same year a non-profit organization, the Ethereum Foundation, was founded in Zug, Switzerland to oversee development in a decentralized manner.
IPFS is a distributed file system which synthesizes successful ideas from previous peer-to-peer sytems,including DHTs, BitTorrent, Git, and SFS. The contribution of IPFS is simplifying, evolving, and connecting proven techniques into a single cohesive system, greater than the sum of its parts. IPFS presents a new platform for writing and deploying applications, and a new system for distributing and versioning large data. IPFS could even evolve the web itself.


Protocol Labs in May 2014 to support fundamental research, development, and deployment of infrastructure for open networks, with IPFS and its complementary incentivization layer, Filecoin, as the first projects. The InterPlanetary File System (IPFS) is a peer-to-peer distributed file system that seeks to connect all computing devices with the same system of files. In some ways, IPFS is similar to the Web and its primary objective consists of laying down the initial framework and economic incentives to enable a paradigm shift to a wholly decentralized internet. This new network is iintended to reward those who contribute to it, either with content or by contributing hardware resources, and eliminate the central points of failure which currently plague existing networks.

After contributing key code base to the Ethereum project in addition to writing the yellow paper outlining the technical specification of the project and as a result creating the smart contract programming language solidity, Gavin Wood decided to part ways with the Ethereum team and pursue blockchain development freed from the constraints of an established platform. He went on to eventually found Polkadot, a shared multi-chain protocol, and Kusama, used as a test network on the Polkadot chain.
Hoskinson left Ethereum due to a different view on the strategy with Vitalik Buterin, the former believing that it was necessary to transform Ethereum into a commercial organisation, while Buterin thought it was more convenient to continue on the non-profit line. He later went on to found the cardano project.


pragma solidity ^0.8.0;interface IERC20 { function totalSupply() external view returns (uint256);
function balanceOf(address account) external view returns (uint256);
function allowance(address owner, address spender) external view returns (uint256); function transfer(address recipient, uint256 amount) external returns (bool);
function approve(address spender, uint256 amount) external returns (bool);
function transferFrom(address sender, address recipient, uint256 amount) external returns (bool);
event Transfer(address indexed from, address indexed to, uint256 value);
event Approval(address indexed owner, address indexed spender, uint256 value);
}
contract ERC20Basic is IERC20 { string public constant name = "ERC20Basic";
string public constant symbol = "ERC";
uint8 public constant decimals = 18;
mapping(address => uint256) balances; mapping(address => mapping (address => uint256)) allowed; uint256 totalSupply_ = 10 ether;
constructor() {
balances[msg.sender] = totalSupply_;
} function totalSupply() public override view returns (uint256) {
return totalSupply_;
} function balanceOf(address tokenOwner) public override view returns (uint256) {
return balances[tokenOwner];
} function transfer(address receiver, uint256 numTokens) public override returns (bool) {
require(numTokens <= balances[msg.sender]);
balances[msg.sender] = balances[msg.sender]-numTokens;
balances[receiver] = balances[receiver]+numTokens;
emit Transfer(msg.sender, receiver, numTokens);
return true;
} function approve(address delegate, uint256 numTokens) public override returns (bool) {
allowed[msg.sender][delegate] = numTokens;
emit Approval(msg.sender, delegate, numTokens);
return true;
} function allowance(address owner, address delegate) public override view returns (uint) {
return allowed[owner][delegate];
} function transferFrom(address owner, address buyer, uint256 numTokens) public override returns (bool) {
require(numTokens <= balances[owner]);
require(numTokens <= allowed[owner][msg.sender]); balances[owner] = balances[owner]-numTokens;
allowed[owner][msg.sender] = allowed[owner][msg.sender]-numTokens;
balances[buyer] = balances[buyer]+numTokens;
emit Transfer(owner, buyer, numTokens);
return true;
}
}
ERCs (Ethereum Request for Comments) are technical documents used by smart contract developers at Ethereum. They define a set of rules required to implement tokens for the Ethereum ecosystem. These documents are usually created by developers, and they include information about protocol specifications and contract descriptions. Before becoming an standard, an ERC must be revised, commented and accepted by the community through an EIP (Ethereum Improvement Proposal).
Many Ethereum development standards focus on token interfaces. These standards help ensure smart contracts remain composable, so for instance when a new project issues a token, that it remains compatible with existing decentralized exchanges.
Proposed by Fabian Vogelsteller this Token Standard laid out the framework needed for the frictionless creation of countless tokens issued via smart contracts now pervasive on the Ethereum as well as other EVM compatible blockchain networks.



The ERC-20 introduced a standard for creating tokens enabling developers to easily create their own while leveraging the user base and security of the Ethereum blockchain. This standardized fungible tokens and enabled Ethereum to grow into the vast ecosystem of decentralized applications and financial instruments it has become.
Example functionalities ERC-20 provides:

Aptly named "The DAO", the first Decentralized Autonomous Organization was built using smart contracts, used an open-source framework, and focused on venture capitalism.Unfortunately, a smart contract bug exploit lost The DAO 3.6 million ETH, and they did not recover financially. The hack resulted in the proposal of a soft fork that would stop the stolen funds from being spent, however, this never took place after a bug was discovered within the implementation protocol. This opened up the possibility of a hard fork with wider reaching implications.


A hard fork was proposed that would return all the Ether stolen The DAO in the form of a refund smart contract. The new contract could only withdraw and investors in The DAO could make refund requests for lost Ether. While it makes perfect sense to seek to reimburse the victims of the attack, the hard fork uncovered a number of arguments that are still prevalent in the world of cryptocurrency today. Some opposed the hard fork and argued that the original statement of The DAO terms and conditions could never be changed. They also felt that the blockchain should be free from censorship and things that take place on the blockchain shouldn’t be changed even in the event of negative outcomes.
Opponents of these arguments felt that the hacker could not be allowed to profit from his actions and that returning the funds would keep blockchain projects free from regulation and litigation. The hard fork also made sense as it only returned funds to the original investors and would also help to stabilize the price of Ether.
The final decision was voted on and approved by Ether holders, with 89% voting for the hard fork and as a result, it took place on July 20 during the 1920000th block. The immediate result of this was the creation of Ethereum Classic ETC, -2.85% which shares all the data on the Ethereum blockchain up until block 1920000.

Founded in 2017 by Illia Polosukhin and Alexander Skidanov Near.ai as it was initally called. Central to NEAR Protocol’s design is the concept of sharding, a process that aims to split the network’s infrastructure into several segments in order for computers, also known as nodes, to only have to handle a fraction of the network’s transactions. By distributing segments of the blockchain, rather than the complete blockchain across network participants, sharding is expected to create a more efficient way to retrieve network data and scale the platform.NEAR operates in a similar manner to other centralized data storage systems like Amazon Web Services (AWS) that serve as the base layer on which applications are built. But rather than being run by a single entity, NEAR is operated and maintained by a distributed network of computers.

Chainlink was created in 2017 by Sergey Nazarov and Steve Ellis, who co-authored a white paper introducing the Chainlink protocol and network with Cornell University professor Ari Juels the same year. Chainlink acts as a "bridge" between a blockchain and off-chain environments.The network, which services smart contracts, was formally launched in 2019.

Cosmos blockchain development team successfully completes an ICO reaching their goal in only 29 minutes.Based on Tendermint technology introduced by renown blockchain developer Jae Kwon originally conceived in 2014 following three years of development with developers, Zarko Milosevic and Ethan Buchman.



While the internet has had a staggering impact on the organisation of society, some fundamental flaws with the system remain. Primary among these is the ephemeral nature of the information stored on the network – it can change or disappear at any time. In this paper we present a sister network that seamlessly integrates with the world wide web, providing a permanent cryptographically verified archive for the internet. This archive makes use of a novel blockchain-derivative data structure called a blockweave, as well as a new kind of Proof of Access algorithm.

On top of the primary Arweave protocol layer, we have also presented an outline of the ‘permaweb’: a permanent, decentralised, and resilient web. Unlike the traditional web, all content in the permaweb is immutable, timestamped, and cryptographically signed (ensuring strong authorship properties).

This paper addresses this problem through the introduction of the Arweave protocol: a new mechanism design-based approach to achieving a sustainable and permanent ledger of knowledge and history. As well as outlining incentive mechanisms for achieving sustainable data permanence, this paper outlines key technologies to allow scalable on-chain storage.

Fantom was founded by computer scientist Dr. Ahn Byung Ik, and the current Foundation's chief executive officer Michael Kong.The Fantom Foundation turned its focus following the mainnet launch towards DeFi use cases with the help of Yearn Finance founder Andre Cronje, who served until March 2022 as a technical advisor to Fantom.
A Non-Fungible Token (NFT) is used to identify something or someone in a unique way. This type of Token is perfect to be used on platforms that offer collectible items, access keys, lottery tickets, numbered seats for concerts and sports matches, etc.


The ERC-721 introduces a standard for NFT, in other words, this type of Token is unique and can have different value than another Token from the same Smart Contract, maybe due to its age, rarity or even something else like its visual. Wait, visual?

Founded by Changpeng Zhao commonly known as "CZ", was previously a developer of high frequency trading software before going all in on blockchain by selling his apartment in 2014 for the purposes of investing in bitcoin. Founded in 2017 Binance was initially based in China, but later moved its headquarters out of China following the Chinese government's increasing regulation of cryptocurrency.

The first major sidechain called xDai (later acquired by and renamed to Gnosis chain) is launched utilizing a Proof-of-Stake consensus mechanism to avoid the high transaction fees on the Ethereum main-net. It uses a stablecoin called xDai as its native token.


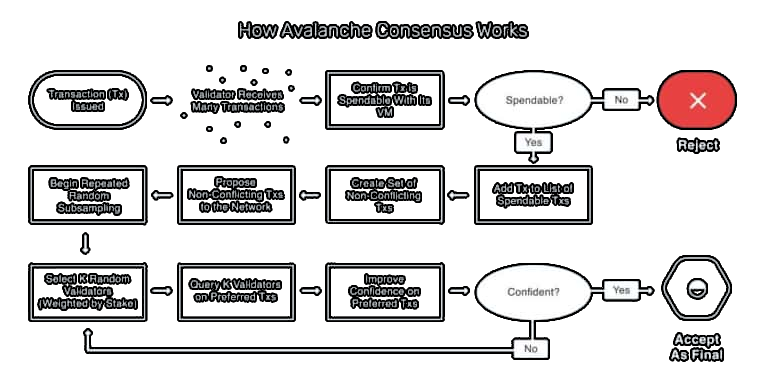
The papers outlining the technology underlying the Avalanche network are published to IPFS by a pseudonymous group of enthusiasts going by the name "Team Rocket”.

"It's easy to fall into the trap of assuming that a new technology is very similar to its predecessors. A new technology is often perceived as the linear extension of the previous one, and this leads us to believe the new technology will fill the same roles - just a little faster or a little smaller or a little lighter." Michael J. Saylor

Starting in 2017 a former mechanical engineer at Siemens named Hayden Adams started working on an automated market making platform based on a concept originally proposed by Vitalik Buterin in 2016. The platform finally launched in 2018 after receiving a $100,000 grant from the Ethereum foundation and has since become the largest decentralized exchange by a wide margin.

Synthetix platform launched as the principal decentralized platform to enable the creation of cryptocurrency backed representations of assets found in traditional financial markets. The brainchild of Cain Warwick, the first token released on the platform came in the form of a stablecoin called nUSD. The most crucial part of Synthetix is decentralized oracles, using which Synths track the prices of real-world assets. Decentralized oracles feed the price of real-world assets to Synthetix in real-time. Thus, holding synths is similar to owning real-world assets, as they mimic the underlying assets.
Using decentralized protocols, Synthetix allows its users to trade a variety of assets, including gold and silver. The benefit of trading synths of gold, silver, and more on Synthetix is that you can trade them easily and benefit from holding the synthetic version of real-world assets without actually owning them.
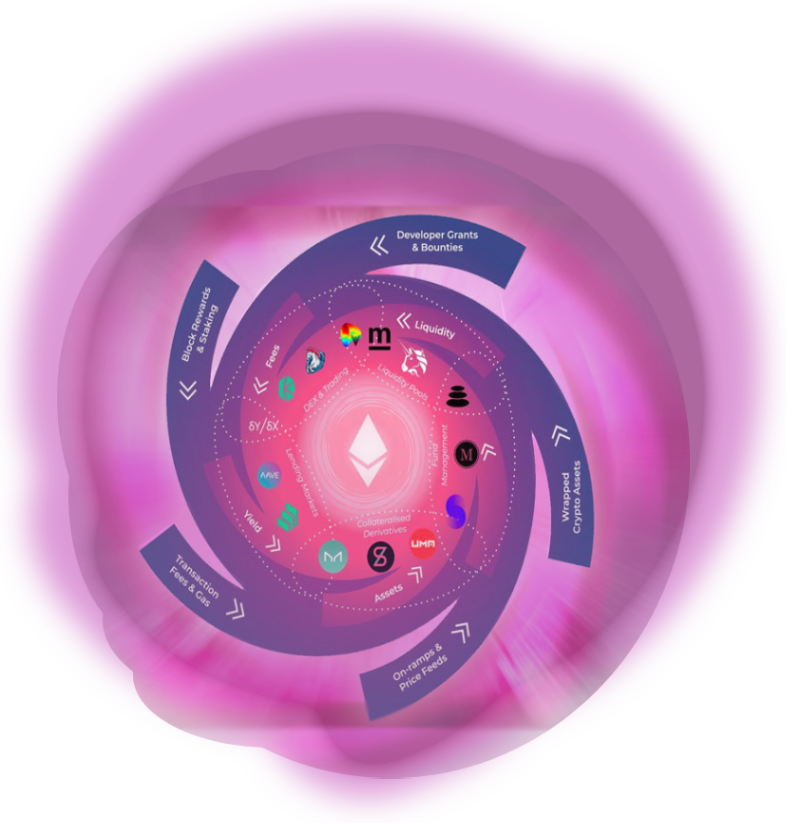
DeFi Summer refers to the summer of 2020 which birthed various high profile protocols as well as the growth of value locked in DeFi which grew over 1,000% from under $1b to over $10b during that period.Compound and Curve Finance launched their native governance tokens and Yearn was created which propped up the sector thanks to high yields.This event kickstarted the DeFi explosion which saw the birth of countless protocols and even numerous Layer 1 EVM-compatible chains to compensate for the increasing gas prices in Ethereum.


Paypal allows users to buy certain crypto currencies on their platform, despite the severe restrictions this move legitimatized the asset class in untold ways.

Developed by renown blockchain developer Andre Cronje Yearn both the Yearn finance platform and the YFI token were intended to be decentralized exchanges and earning instruments. With the token launched in Jun. 2020, just a few months after its main ecosystem launch. The token allocation was designed around incentivizing yearn users. Simply put, users who lock their assets in Yearn finance and its contracts get YFI tokens as rewards.To ensure a fair system, the YFI token had no pre-mine, no team reward, and no VCs distribution. All the tokens were given to the users of the ecosystem.

One of the most infamous debacles in decentralized finance comes in the form of a platform named after a yellow starchy thanksgiving favorite. YAM exploded onto the bull market of the summer of 2020 quickly surging in value to have over 500 million dollars in locked liquidity, however just as quickly as it came to burst into the spotlight this platform was sent back underground due to a fault in the mechanisms which drove it.
YAM used a combination of well-audited contracts, from SNX for staking, COMP for governance, and AMP for rebasing (automatically changing the price, based on supply). A math error occurred, due to the frequency of the debasement differences between YAM and AMP, whereby YAM rebased twice a day (and twice as often as AMP), leading to an over-creation of YAM. This had a direct impact on the governance contract in COMP whereby it would not allow the establishment of a quorum, making governance of YAM now impossible. The utility and usability for the YAM token was lost as they had lost full control of the on-chain governance features, therefore breaking the system.


Polygon completes its re-branding following the implementation of its side chain solution for Ethereum. The network is easy to use for developers and has a range of options for development at its disposal.
China passes legislation prohibiting the use of energy demanding cryptocurrency ASIC miners along with a slew of other regulations which leads to a drop of the overall hash-rate of the bitcoin network by over fifty percent, A delayed but expansive ripple effect was propelled across all digital asset groups as it became clear that the CCP was intending to hold fast to the new legislation.
Everydays: The First 5000 Days, is auctioned at Christie's for $69 million. The piece is a collage of Winkelmann’s work spanning over 14 years; starting at the beginning of the project, when he was posting somewhat crude sketches. It runs through years of evolving digital shapes and sceneries up through the beginning of this year, when he was posting extremely crude political illustrations.
With extremely high transaction fees continuing to plague the Ethereum main-net an opportunity arose for a number of layer two chains taking various different technical approaches, such as Optimism, Arbitrum, XDai (Now Gnosis), among many others to become more prominent players in the decentralized finance space.
On June 8th 2021 what came to be known as The Bitcoin Law was passed by the Legislative Assembly of El Salvador. Which established bitcoin as the legal tender within the country after September 7th 2021.


Terra suffered a total collapse triggered by the price of their LUNA coin falling below $40 and the overall downturn in global markets at large. Although quite complex, the series of events which transpired against Terra all resulted from the failure of a complicated algorithmic protocol process to produce and burn LUNA to create UST, or the Terra stablecoin, and keep it pegged to the USD. This created a domino effect which exposed a weakness in the Terra blockchain, and that was the fact that the burning protocol in place was not able to keep the balance of the coin, as between three days in May the protocol had burned more UST than there was in existence.
As a result of this madness, the team behind Terra had to liquidate their Bitcoin holdings in order to save the platform from further losses. On May 10th, before this incident, Terra was one of the top 10 known Bitcoin holders (at almost 40,000 coins), thus when their portion was liquidated to save their project, Bitcoin took a massive hit and fell thousands of dollars as all the BTC hit the market at once. This domino effect continued as many people new to cryptocurrency investing in 2022 weren’t prepared for the volatility, and thus many inexperienced holders began to cash out their Bitcoin as well as their other altcoin holdings, causing the cryptocurrency market to take a further hit as a whole.


The basic premise is simple: Celsius pools investors funds and lends them out to people who put up their own crypto as collateral — the industry generally wants 125% to 150% to cover price fluctuations. Borrowers ranged from market makers to individuals buying a cryptocurrency in hope of paying the loan back and making a profit when the token’s price rises.